
Lockdown Your iPhone: A Comprehensive Guide to Protecting Your Device from Hacking and Malware
Related Articles: Lockdown Your iPhone: A Comprehensive Guide to Protecting Your Device from Hacking and Malware
- Supercharge Your IPhone: The Ultimate Guide To The Best IPhone Chargers For Faster, Safer Charging
- Unleash The Power Of Siri: Mastering Your IPhone’s Voice Assistant
- IPhone Vs. Android: Why IPhone Still Leads In 2024
- IPhone Vs. Android: Why IPhone Still Leads In 2024
- Unlock Your IPhone’s Potential: A Guide To Personalization And Unique User Experiences
Introduction
Join us as we explore Lockdown Your iPhone: A Comprehensive Guide to Protecting Your Device from Hacking and Malware, packed with exciting updates
Video about Lockdown Your iPhone: A Comprehensive Guide to Protecting Your Device from Hacking and Malware
Lockdown Your iPhone: A Comprehensive Guide to Protecting Your Device from Hacking and Malware

In today’s digital world, our iPhones are more than just phones. They are our wallets, our diaries, our entertainment hubs, and even our keys to our homes. This makes them incredibly valuable targets for hackers and malware creators. While Apple has built a robust security system into iOS, it’s crucial to understand that no device is truly impenetrable.
This comprehensive guide will equip you with the knowledge and tools to safeguard your iPhone from the ever-evolving threats of hacking and malware. We’ll cover everything from basic security practices to advanced techniques, ensuring your iPhone remains a secure and reliable companion.
Understanding the Threat: Hacking and Malware Explained
Before we delve into protection strategies, let’s understand the enemies we’re facing:
Hacking: Hacking refers to unauthorized access to your iPhone’s data, apps, or even the device itself. Hackers employ various methods, including:
- Phishing: Tricking you into clicking malicious links or providing personal information through fake websites or emails disguised as legitimate sources.
- Social Engineering: Manipulating you into revealing confidential information through psychological tactics, such as impersonating a trusted source or creating a sense of urgency.
- Malware: This refers to malicious software designed to steal data, disrupt your device’s functionality, or gain unauthorized access to your iPhone.
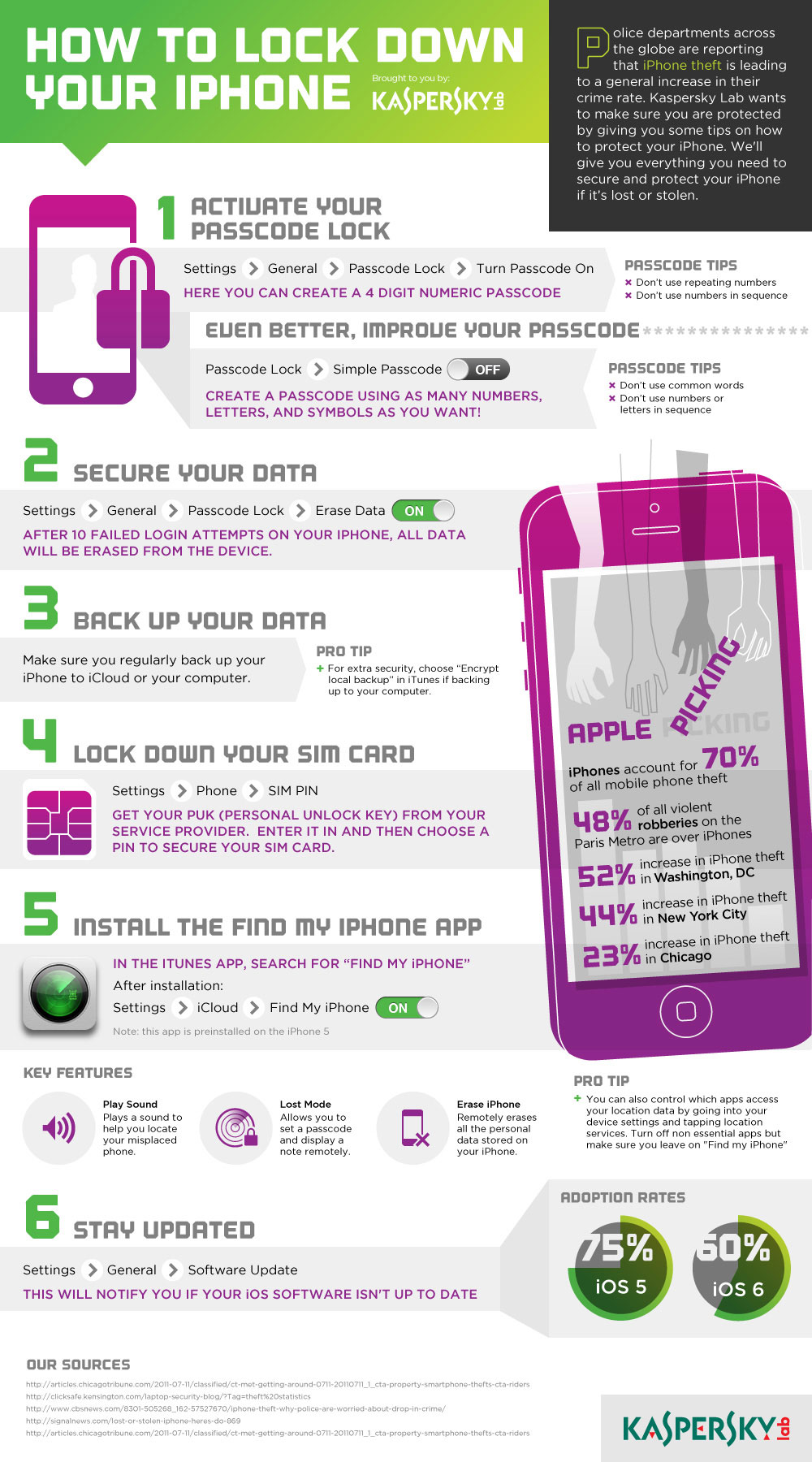
Malware: Malware is a broad term encompassing various types of malicious software targeting iPhones. Here are some common threats:
- Spyware: This type of malware secretly monitors your activities, stealing data like passwords, browsing history, and even microphone recordings.
- Adware: These programs bombard you with unwanted ads, often redirecting you to malicious websites or installing additional malware.
- Ransomware: Ransomware encrypts your data, making it inaccessible until you pay a ransom to the attackers.
- Trojan Horses: These disguised as legitimate apps or files, often downloaded from untrusted sources, can grant hackers remote access to your device.

Protecting Your iPhone: A Multi-Layered Approach
Securing your iPhone requires a multi-layered approach, combining proactive measures with ongoing vigilance. Here’s a detailed breakdown of essential strategies:
1. Keep Your iPhone Updated:
- iOS Updates: Apple regularly releases iOS updates to address security vulnerabilities and patch known exploits. Ensure you’re running the latest version of iOS by navigating to Settings > General > Software Update.
- App Updates: Similarly, keep your apps updated. Developers frequently release updates to fix security flaws in their apps. Check for updates in the App Store regularly.
2. Strong Passwords and Biometric Authentication:
- Strong Passwords: Use a unique and complex password for your Apple ID and avoid using easily guessable combinations like "123456". Consider using a password manager to generate and store strong passwords securely.
- Biometric Authentication: Enable Touch ID or Face ID for added security. These features prevent unauthorized access to your iPhone, making it harder for hackers to gain entry.
3. Be Wary of Suspicious Links and Attachments:
- Phishing Scams: Never click on links or open attachments from unknown sources, even if they appear to come from a trusted contact. Always verify the sender’s identity before clicking on any link.
- Malicious Websites: Be cautious when browsing websites, especially those you haven’t visited before. If a website looks suspicious or requests excessive permissions, avoid accessing it.
4. Install Reputable Security Apps:
- Anti-Malware Software: While iOS is inherently secure, there are dedicated anti-malware apps available for iPhones. These apps can scan your device for potential threats and provide real-time protection.
- VPN (Virtual Private Network): A VPN encrypts your internet traffic, making it difficult for hackers to intercept your data. This is particularly important when using public Wi-Fi networks.
5. Be Mindful of App Permissions:
- Limited Permissions: Carefully review app permissions before installing an app. Only grant access to essential permissions and deny any requests that seem unnecessary.
- App Store Only: Download apps exclusively from the official App Store. Avoid downloading apps from third-party sources, as they may contain malware.
6. Use Two-Factor Authentication:
- Enhanced Security: Enable two-factor authentication for your Apple ID. This requires you to enter a verification code sent to your trusted device, making it much harder for hackers to access your account.
- Recovery Keys: Keep your recovery keys safe. These keys can be used to recover your account if you lose access to your device or forget your password.
7. Be Cautious with Public Wi-Fi:
- Unsecured Connections: Public Wi-Fi networks are often insecure, making your data vulnerable to eavesdropping. Avoid using public Wi-Fi for sensitive activities like online banking or shopping.
- VPN Protection: When using public Wi-Fi, use a VPN to encrypt your traffic and protect your data from prying eyes.
8. Regularly Backup Your iPhone:
- Data Protection: Regularly backup your iPhone to iCloud or your computer. This allows you to restore your data if your device is lost, stolen, or damaged.
- Data Recovery: Backups also help you recover data if your iPhone is infected with malware or ransomware.
9. Enable "Find My iPhone":
- Device Tracking: Enable "Find My iPhone" in Settings > Find My. This feature allows you to locate your iPhone if it’s lost or stolen.
- Remote Lock and Erase: You can remotely lock your iPhone or erase its data if it falls into the wrong hands.
10. Stay Informed and Updated:
- Security News: Stay informed about the latest security threats and vulnerabilities. Subscribe to security newsletters or follow reputable cybersecurity blogs.
- Security Updates: Keep your operating system and apps updated regularly to patch security vulnerabilities and address known exploits.
High-Value Keywords:
- iPhone security
- iPhone hacking
- iPhone malware
- iOS security
- iPhone protection
- cybersecurity
- data privacy
- phishing scams
- social engineering
- anti-malware
- VPN
- two-factor authentication
- strong passwords
- biometric authentication
- app permissions
- public Wi-Fi security
- data backup
- Find My iPhone
Conclusion: A Secure iPhone is a Powerful Tool
Protecting your iPhone from hacking and malware is an ongoing process. By following the strategies outlined in this guide, you can significantly reduce the risk of falling victim to cyber threats. Remember, vigilance, caution, and staying informed are key to keeping your iPhone secure and your data safe.
Investing in your iPhone’s security is an investment in your digital well-being and peace of mind. By taking proactive measures and staying informed about emerging threats, you can ensure your iPhone remains a reliable and trustworthy companion in the digital world.

Closure
We hope this article has helped you understand everything about Lockdown Your iPhone: A Comprehensive Guide to Protecting Your Device from Hacking and Malware. Stay tuned for more updates!
Make sure to follow us for more exciting news and reviews.
Feel free to share your experience with Lockdown Your iPhone: A Comprehensive Guide to Protecting Your Device from Hacking and Malware in the comment section.
Stay informed with our next updates on Lockdown Your iPhone: A Comprehensive Guide to Protecting Your Device from Hacking and Malware and other exciting topics.

















