
Lockdown Your iPhone: Ultimate Guide to Protection from Hacking and Malware
Related Articles: Lockdown Your iPhone: Ultimate Guide to Protection from Hacking and Malware
- The IPhone 15: A Game Changer For Photography Enthusiasts
- iPhone 16 vs iPhone 15: Is It Time to Upgrade?
- Unleash The Power: Maximizing Your IPhone 16 Battery Life
- Mastering Security: A Comprehensive Guide To Setting Up Face ID And Securing Your IPhone 16
- Unlock Your Potential: Top IPhone Tips For Students
Introduction
Discover everything you need to know about Lockdown Your iPhone: Ultimate Guide to Protection from Hacking and Malware
Video about Lockdown Your iPhone: Ultimate Guide to Protection from Hacking and Malware
Lockdown Your iPhone: Ultimate Guide to Protection from Hacking and Malware

Your iPhone is a treasure trove of personal information – from your banking details and social media accounts to your private photos and messages. It’s a tempting target for hackers and malware creators, but don’t worry! With the right knowledge and precautions, you can keep your iPhone safe and secure.
This comprehensive guide will walk you through the essential steps to protect your iPhone from hacking and malware. We’ll cover everything from basic security practices to advanced techniques, equipping you with the knowledge to safeguard your digital life.
Understanding the Threats
Before we delve into the specifics, let’s understand the threats you’re facing:
1. Phishing Attacks: These scams use deceptive emails, text messages, or websites to trick you into revealing sensitive information like passwords, credit card details, or even your Apple ID.
2. Malware: Malicious software designed to steal your data, spy on your activities, or damage your device. While iPhones are known for their robust security, they’re not immune to malware, especially with the rise of sideloading apps and jailbreaking.
3. Man-in-the-Middle (MitM) Attacks: These attacks intercept your communication with a website or service, allowing hackers to steal your data or inject malicious code.
4. Physical Access: If someone gains physical access to your iPhone, they can potentially bypass security measures and access your data.
5. Social Engineering: Hackers often use psychological manipulation to trick you into giving them access to your device or revealing sensitive information.
Securing Your iPhone: A Step-by-Step Guide
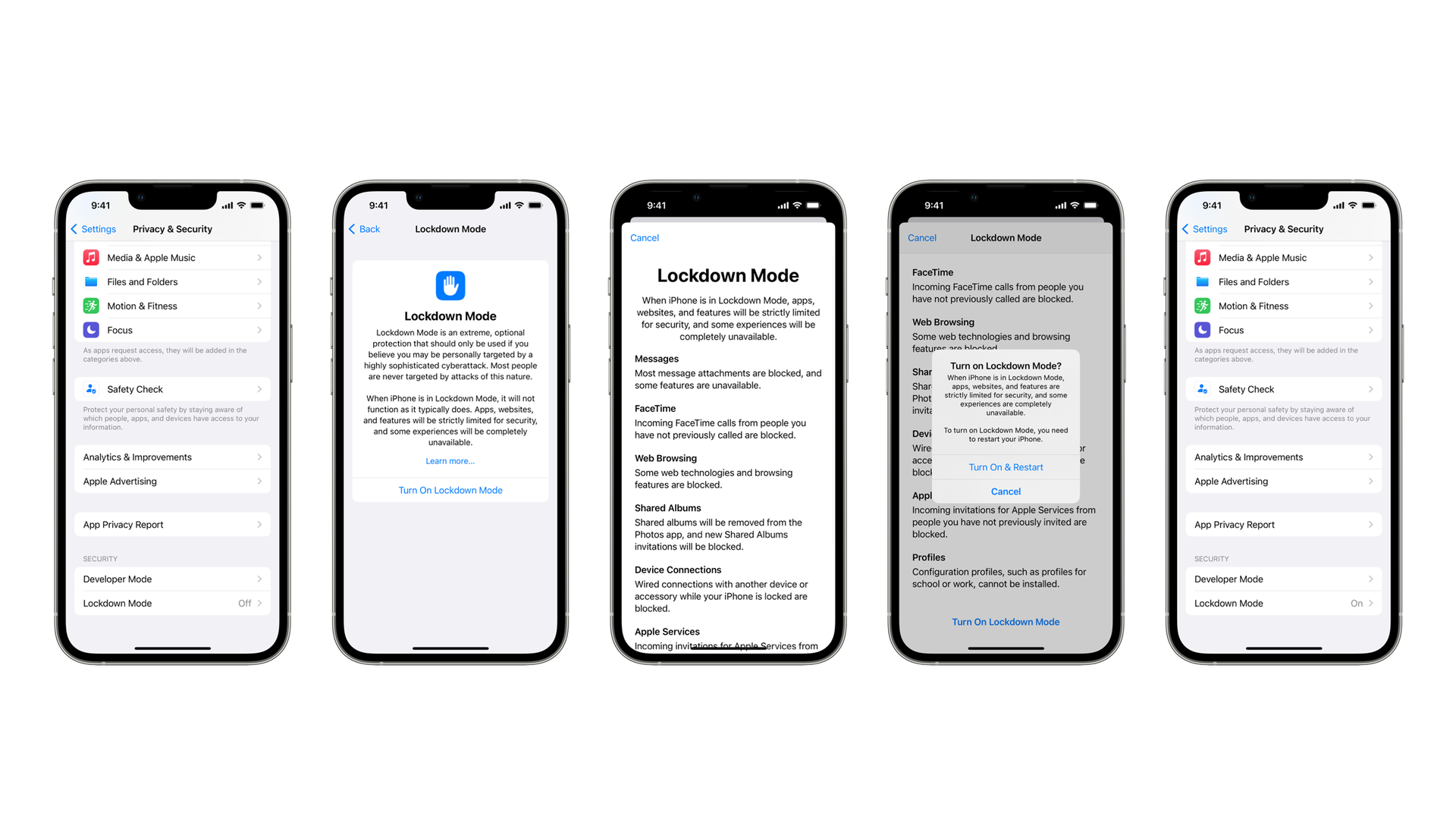
Now, let’s dive into the practical steps you can take to protect your iPhone:
1. Keep Your Software Updated:
- iOS Updates: Apple regularly releases security updates to patch vulnerabilities. Make sure you enable automatic updates to ensure your iPhone has the latest security features.
- App Updates: App developers also release updates to fix security flaws. Enable automatic app updates to keep your apps secure.

2. Use Strong Passwords and Two-Factor Authentication:
- Strong Passwords: Use unique, complex passwords for your Apple ID and other accounts. Avoid using common phrases or personal information. Consider using a password manager to generate and store strong passwords.
- Two-Factor Authentication (2FA): This adds an extra layer of security by requiring a code from your trusted device, like your iPhone, in addition to your password. Enable 2FA for your Apple ID and other important accounts.
3. Be Cautious About Downloading Apps:
- Official App Store: Always download apps from the official Apple App Store. Avoid downloading apps from third-party sources, as they may contain malware.
- App Permissions: Carefully review the permissions requested by apps before installing them. If an app requests access to sensitive data, like your contacts or location, consider whether it’s truly necessary.
4. Protect Your Data:
- Password Protect Your iPhone: Set a strong passcode for your iPhone and enable "Erase Data" after ten failed attempts to prevent unauthorized access.
- Use Touch ID or Face ID: These biometric authentication methods provide an extra layer of security.
- Data Encryption: Enable "Find My iPhone" and "Data Protection" to encrypt your data, making it difficult for hackers to access even if your phone is lost or stolen.
- Secure Wi-Fi Networks: Avoid connecting to public Wi-Fi networks unless absolutely necessary. Use a VPN (Virtual Private Network) to encrypt your internet traffic when using public Wi-Fi.
5. Be Wary of Suspicious Links and Messages:
- Don’t Click Suspicious Links: If you receive an email or text message with a link that looks suspicious, don’t click on it. Check the sender’s address and be cautious about links that promise something too good to be true.
- Be Skeptical of Phishing Attempts: Phishing attacks often try to create a sense of urgency or fear. If you receive a message asking for sensitive information, verify its legitimacy before providing any details.
6. Consider Additional Security Measures:
- Anti-Malware Software: While iPhones are generally less susceptible to malware than other platforms, anti-malware apps can provide an extra layer of protection.
- VPN: A VPN encrypts your internet traffic, making it difficult for hackers to intercept your data. It’s especially useful when using public Wi-Fi networks.
- Security Keys: Use a security key (like a YubiKey) for your Apple ID to add an extra layer of protection. Security keys are physical devices that plug into your iPhone, making it virtually impossible for hackers to access your account.
7. Stay Informed and Up-to-Date:
- Stay Updated on Security Threats: Follow reputable security news sources and blogs to stay informed about emerging threats and vulnerabilities.
- Learn About Security Best Practices: Continuously learn about new security practices and techniques to protect your iPhone.
8. Be Proactive in Protecting Your Data:
- Back Up Your Data: Regularly back up your iPhone to iCloud or your computer. This ensures you can restore your data if your phone is lost, stolen, or damaged.
- Be Mindful of Your Online Activities: Be cautious about the information you share online and avoid posting sensitive information on social media.
- Monitor Your Accounts: Regularly check your bank statements and credit card bills for any unauthorized transactions.
High-Value Keywords:
- iPhone Security
- iPhone Hacking
- iPhone Malware
- Protect iPhone
- iPhone Privacy
- iPhone Data Protection
- iPhone Security Tips
- iPhone Security Best Practices
- iPhone Security Settings
- iPhone Security Guide
- iPhone Security Software
- iPhone Security Apps
- iPhone Security Features
- Secure iPhone
- iPhone Security Measures
- iPhone Safety
- iPhone Data Security
- iPhone Password Security
- iPhone Two-Factor Authentication
- iPhone Phishing
- iPhone Man-in-the-Middle Attack
High CPC Keywords:
- Best iPhone Security Apps
- How to Secure iPhone
- How to Protect iPhone from Hacking
- iPhone Security Software Review
- iPhone Data Encryption
- iPhone Anti-Malware
- iPhone VPN
- iPhone Security Key
- iPhone Data Backup
- iPhone Security Tips for Beginners
Conclusion
Securing your iPhone requires an ongoing effort. By following these steps and staying informed about the latest security threats, you can significantly reduce the risk of hacking and malware. Remember, your digital life is precious, and it’s your responsibility to protect it.
Beyond the Basics: Advanced Security Techniques
For those seeking advanced protection, consider these additional techniques:
- Jailbreaking: While it can offer more customization, jailbreaking your iPhone compromises its security, making it more vulnerable to hacking and malware.
- Sideloading Apps: Installing apps from outside the official App Store can expose your iPhone to malware.
- Using a Private Browser: Private browsers like Brave or DuckDuckGo can enhance your privacy by blocking trackers and preventing websites from collecting your browsing data.
- Monitoring Your iPhone Activity: Use built-in tools like "Find My iPhone" and "Screen Time" to monitor your device activity and identify any suspicious behavior.
- Using a Security Audit Service: Professional security audits can identify vulnerabilities in your iPhone and provide recommendations for strengthening your security posture.
Remember, staying informed and proactive is key to maintaining your iPhone’s security. Continuously update your knowledge, adapt your security practices, and be vigilant in protecting your digital life.
Closure
We hope this article has helped you understand everything about Lockdown Your iPhone: Ultimate Guide to Protection from Hacking and Malware. Stay tuned for more updates!
Make sure to follow us for more exciting news and reviews.
We’d love to hear your thoughts about Lockdown Your iPhone: Ultimate Guide to Protection from Hacking and Malware—leave your comments below!
Keep visiting our website for the latest trends and reviews.

















